Que Es Exploits En Seguridad Informatica are a flexible option for organizing tasks, intending events, or developing expert styles. These templates supply pre-designed designs for calendars, planners, invitations, and much more, making them optimal for personal and specialist usage. With very easy personalization options, individuals can tailor typefaces, shades, and material to match their particular needs, conserving effort and time while preserving a sleek look.
Whether you're a pupil, company owner, or creative expert, printable editable templates assist streamline your process. Offered in different styles and layouts, they are perfect for enhancing productivity and creativity. Discover and download these templates to raise your jobs!
Que Es Exploits En Seguridad Informatica

Que Es Exploits En Seguridad Informatica
Send your customized invoices via email or print them out Save your templates so that you can edit each one and change it as necessary Update your invoice Create and send invoices as a PDF attachment using over 100 professional invoice templates. Email invoices directly, get paid by card. Fast & Secure!
Downloadable Free Invoice Templates

Exploit
Que Es Exploits En Seguridad InformaticaEditable free invoice templates. Explore our invoice templates to help you easily create your own design online in minutes. Free Printable Invoice To create a free invoice just fill out the template below To print download or send your invoice for free click the save button
Download a variety of beautifully designed invoice templates for free. Over 100 different invoice templates available and ready for you to use. Seguridad Inform tica A Lo Jabal Blog De Seguridad Informatica Qu Es Un Bug Inform tico Niveles De Gravedad En Los Ciber errores
100 Free Invoice Templates Print Email Invoices

Free Roblox Exploit No Keys System 2021 YouTube Video Roblox
Need an easy and professional way to invoice clients Download this free PDF invoice time tracking spreadsheet template just fill in the blank fields Keeping Your Company Exploit Free Kaspersky Official Blog
Design your own official invoice for any type of business by customizing our free and printable invoice templates Integridad Inform tica Qu Es Y C mo Proteger Los Datos Grupo Atico34 Qu Son Los Exploits Y Cuales Son Sus Vulnerabilidades Mexis
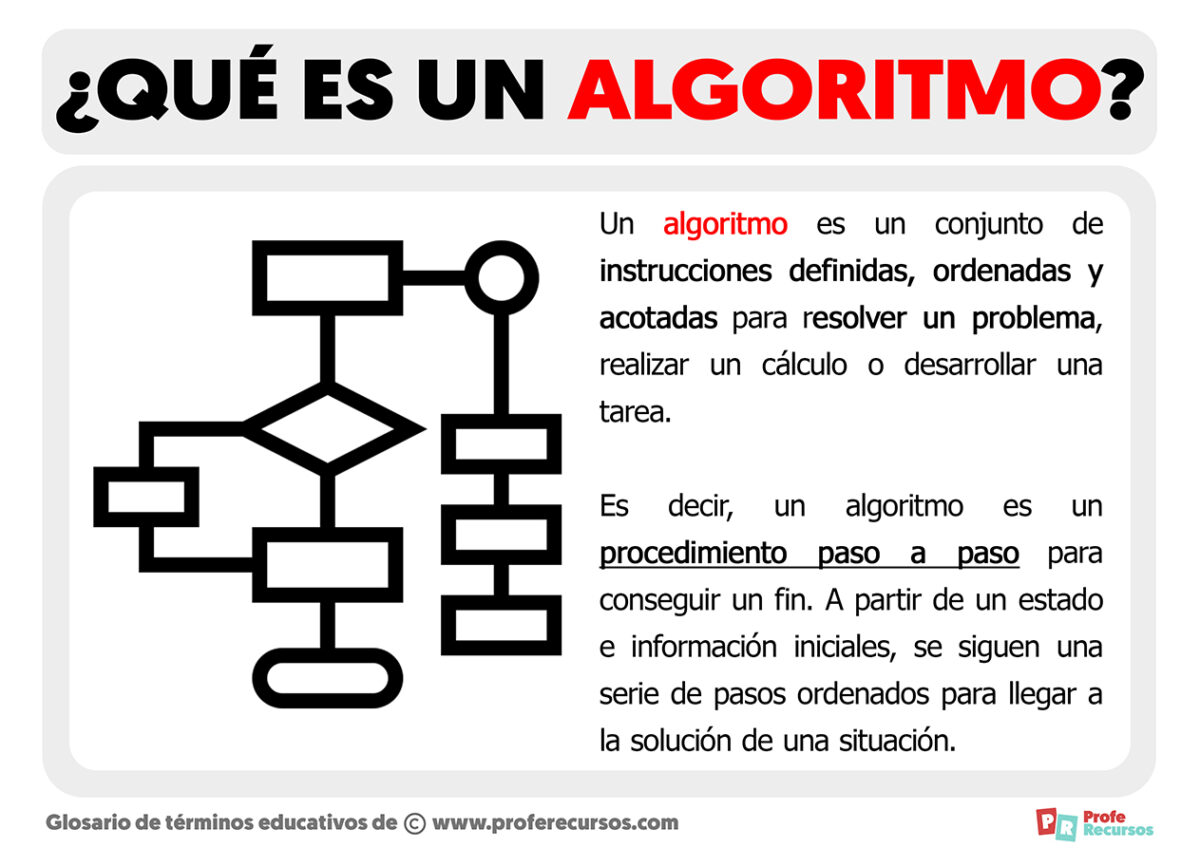
Tipos De Algoritmos Y Ejemplos Image To U

Exploit Db

Seguridad Informatica Mind Map

Pin En Seguridad Web

Qu Es Una Vulnerabilidad Y Un Exploit

MARCO LEGAL DE LAS TIC EN COLOMBIA Mind Map

Tipos De Vulnerabilidades Ciberseguridad Informatica Seguridad

Keeping Your Company Exploit Free Kaspersky Official Blog

What Is Zero Day Exploit All You Need To Know Phemex Blog
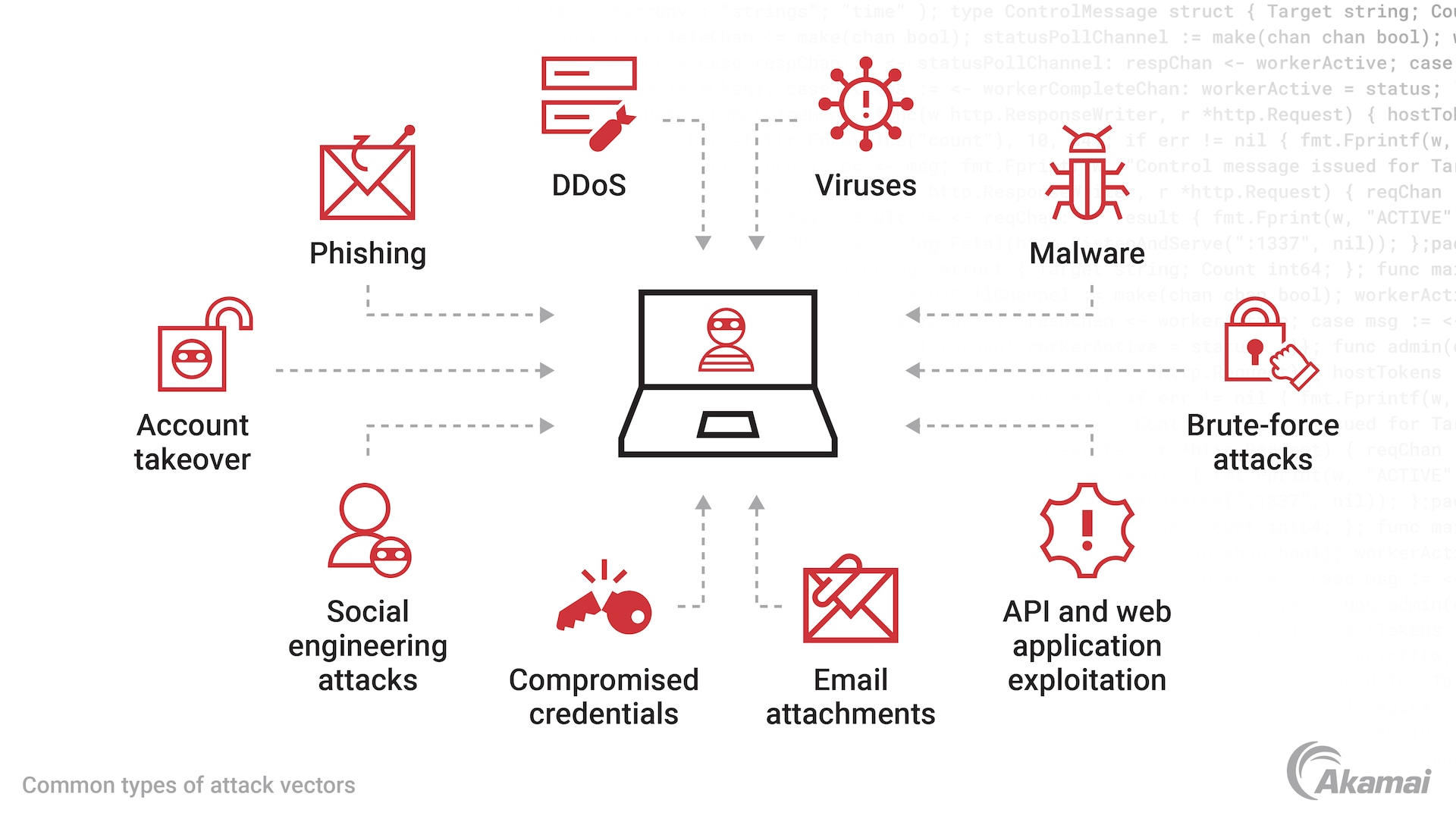
What Is Cybersecurity Or Cyber Security Akamai